TCP Wrappers are versatile, sophisticated, and surprisingly easy to use, and they can secure your servers from attack with run-time ACL reconfiguration. On some Unix-like systems, rather than just responding to probes on those open ports, PortSentry actually opens those unused ports and almost becomes a Honeypot — which has its pros and cons. Do you have a sentry to keep an eye on your servers? An example might be an FTP client that opens up ports outside of the privileged port range anything from port to , which requires the FTP server to connect back to you, opening another port. If you are using the advanced detection option you need to be careful that you don't make a hair trigger situation. 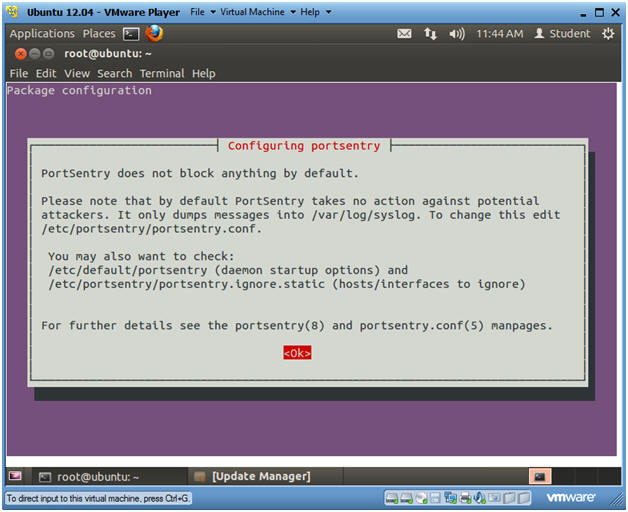
| Uploader: | Mukazahn |
| Date Added: | 28 December 2014 |
| File Size: | 26.61 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 32729 |
| Price: | Free* [*Free Regsitration Required] |
When it comes to PortSentry, simplicity is the key to its efficacy.
The cloud is making HPC more affordable than ever — but choose your configuration carefully! In the olden days, the Internet was without a porfsentry a nicer place. Sadly, the Internet is no longer like that. New Style - The format used when extended option processing is enabled.
This mode requires a full connect and is very hard to spoof. On some Unix-like systems, rather than just responding to probes on those open ports, PortSentry actually opens those unused ports and almost becomes a Honeypot — which has its pros and cons.
Akin to leaving your front door unlocked when you went shopping, you could leave your email accessible with password and no-one would even bat an eyelid.
In standard, basic port-bound modes, it runs in the background and reports any violations, whereas in Stealth modes, PortSentry will use a raw socket to monitor all incoming packets, and if a monitored port portsenrty probed, it will block the host. PortSentry is part of SentryTools.
To ensure that the data on your computers remains accessible only by you and those with whom you want to share, we look at the advantages of combining TCP Wrappers and port knocking. Do you have a sentry to keep an eye on your servers? This daemon will watch unused ports for activity and depending on how it is configured take action upon excessive access to watched ports.
Retrieved from " https: However, the administration side looks a bit more complicated: Do I have shell access or terminal access? PortSentry is clever enough to consider this safe traffic, and this mechanism could even be referred to as using a rudimentary stateful inspection engine, which for software of its age is a little pkrtsentry.
Anything higher is probably not necessary.
Ethernet is so popular because it simply works and is inexpensive. TCP Wrappers are versatile, sophisticated, and surprisingly easy to use, and they can secure your servers from attack with run-time ACL reconfiguration. Often times before an intrusion attempt, one might first scan a machine to look for potential security holes, making this program the defender on the front lines of the cyber battlefield. The days of the alleged unpatched Windows Server being infected with malware within 10 seconds of being plugged into the Internet paints a picture of where lortsentry are today with our precious but flawed Internet.
Customizing PortSentry
The default is 0 which portsdntry react immediately. Incidentally, PortSentry heralds from those innocent and forgotten times and is well over a decade old; amazingly, it still does its job very well.
Some of you may even want this though. A value of 1 or 2 will reduce false alarms.
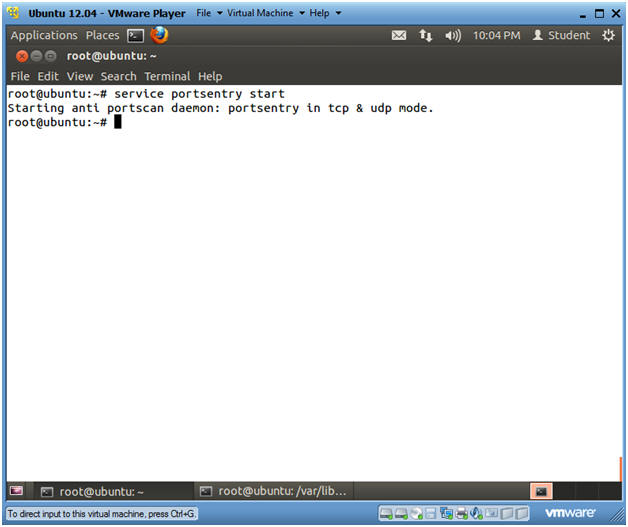
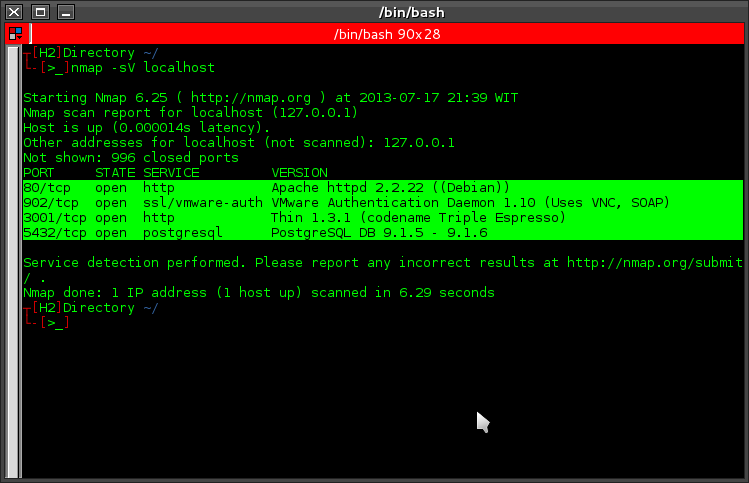
Ubuntu: Lesson Installing and Testing PortSentry against NMAP
We take a closer look. The most sensitive modes are those used by Advanced Stealth scan portsejtry. These are not the same, and careful knowledge must be used when interacting with a shell compared with a terminal.
TCP Stealth tries to do something similar, but it takes a more sophisticated approach. Save money and gain insights by bringing the power of high-performance computing to your enterprise environment. The various modes of PortSentry. If you are using the advanced detection option you need to be careful that you don't make a hair trigger situation. Port scans for finding vulnerable services are nothing new, and port knocking as a defense has been around for a while, too.
A good example of portsentry in action, is that if the machine was port-scanned, it would be blocked and unable to perform further scanning or make attempts at exploiting the machines vulnerabilities.
You can explicitly ask PortSentry to ignore certain ports which can be key when running a particularly reactionary configuration to protect legitimate traffic.
PortSentry From Gentoo Wiki.

No comments:
Post a Comment